7 Top Tips For Enterprise Live Streaming: Scale And Security
Enterprise live streaming lets you broadcast your business meetings, conferences, and private classes to your audience of employees, clients, or students.
These are intended to be private events and may involve discussion of confidential information about your business or your clients.
So, of course, you don’t want any uninvited guests disrupting the stream, stealing insider information, or accessing paid content that your legitimate viewers bought tickets to watch.
How can you keep your events private while streaming to a large audience?
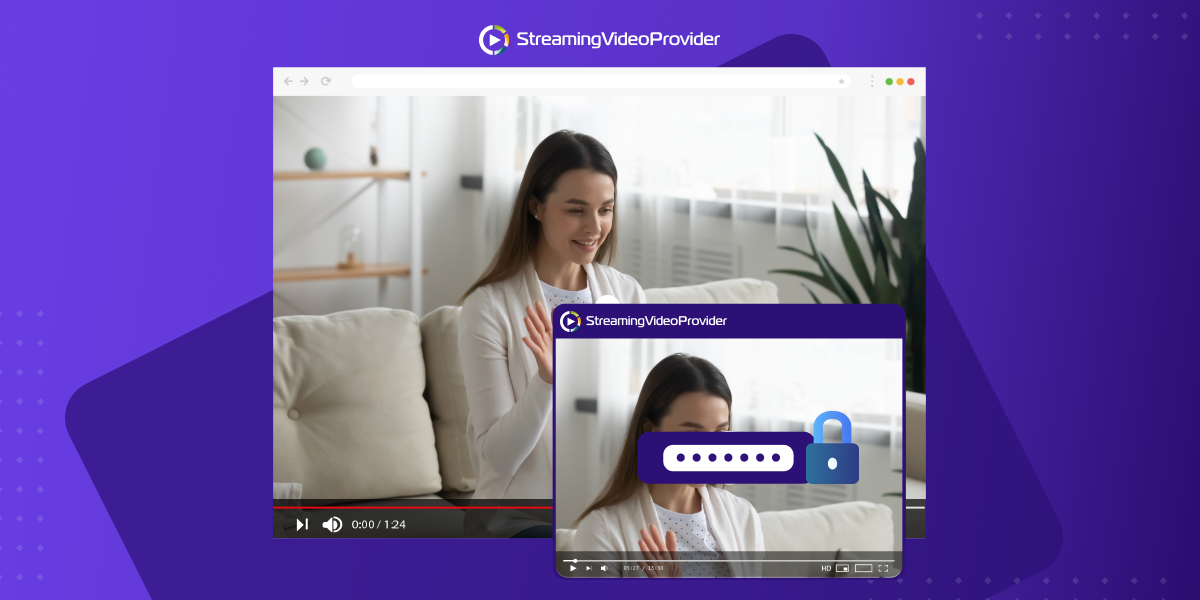
1. Two-Factor Authentication

Two-factor authentication (2FA) is a reliable security measure that is used by many online services, not just for live streaming. This type of protection is difficult to get around and fully automated, making it great for use on a large scale. For example, when doing conference live streaming.
When 2FA is enabled, users start the login process by providing their username and password. If these are valid, 2FA will send a randomly generated password to the user via a third-party app or text-based authentication.
Then, the user can enter the authentication password to access the stream. This password will only be valid for a few minutes at most, depending on the 2FA system in use.
Whenever the authentication process is completed successfully, all other users using those account details will be kicked off the stream.
In effect, 2FA requires access to the code used for authentication as well as a username and password for someone to log into your stream.
This makes it harder for unauthorized viewers to watch using a stolen account. It also prevents users from sharing account details which prevents them from sharing PPV tickets or re-selling their access to the stream.
Device-based 2FA systems such as smartphone authenticator apps can be a bit more secure than those reliant on email, as they require physical access to the user’s device to complete authentication.
However, they are somewhat less convenient for your users, as they will have to install and set up an authenticator app instead of simply confirming their contact details via email or text message.
2. Video Encryption

Video streams can be intercepted by a third party on their way to the intended audience via packet sniffing.
Once your stream data has been intercepted in this way, it could be recorded and uploaded to unofficial sites for anyone to watch. It could even be streamed elsewhere with a slight delay while your official stream is still live.
Stream encryption “scrambles” your stream to render it unusable to any third parties who might intercept it. Only users watching through your intended video player on an approved site will have the decryption key necessary to view the stream.
3. Track Password Usage
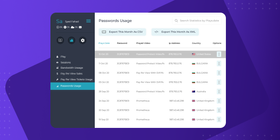
Locking your stream with a password is an obvious first step to keeping your stream private, but it can do more than just keep out people who don’t have the password.
If you use a streaming service that tracks password usage, you will also have a record of who used a password and when they used it.
This makes it easier to spot and remove anyone who is using a password they should not have access to.
By the way, 22% of people have shared their password to a streaming service with a friend or family, and 66% use the same password for multiple accounts.
This means that, if another account gets compromised, an attacker may also know the password used to access your stream.
Furthermore, tracked passwords allow for more detailed control of how your streams can be accessed.
Depending on the situation, you can provide a single password that will give unlimited access to your content and streams, letting you give online students permanent access to your resources, for example.
For example, when you’re setting up a one-time paid event with StreamingVideoProvider, you can create passwords that only unlock a specific video, expire after a certain date, or only allow a limited number of views before access is revoked. This makes tracked passwords one of the most flexible ways to secure enterprise live streams.
Even though we recommend using strong passwords that are unique to your streams, it’s a good idea to keep them memorable, after all.
According to a 2019 study by Google, 75% of Americans are frustrated with the number and complexity of passwords they need to remember.
5. Use Geo-Blocking
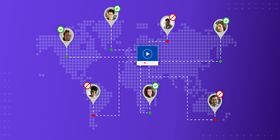
Geo-blocking lets you specify areas where you don’t want your stream to be available for viewing or lock your stream to only be viewable in certain areas.
If you know your entire audience exists within a few geographic regions, for example, this can be a very powerful feature.
For example, when you are streaming an internal meeting and all of your employees live within the same city, this is an easy way to prevent anyone outside that city from tuning into the stream.
6. IP Address Whitelists

An IP address whitelist is a list of network addresses that are allowed to connect to the stream. Any connection not on the list or within the acceptable IP range will be rejected and the viewer will be unable to watch. These can be used in a range of scenarios.
For internal meetings, a whitelist can limit connections to IP ranges owned by your business to ensure only attendees from within your business will be allowed.
Adding single IP addresses instead of a range lets you give access to only specific devices within your business network.
IP whitelists can also be used at a larger scale to give access to audiences when selling tickets to an online event or teaching an online class.
However, they can take more effort to manage at this scale.
Most home connections do not provide a static IP address that you can permanently add to your whitelist. Instead, they assign a dynamic IP address that changes every time the user connects.
As a result, you would need to get the current IP address of every audience member and remove their old address from the whitelist before every stream, or some of your valid users will be locked out. Keep in mind that anyone using a VPN will not be able to access the meeting either as their IP address will change.
7. Restrict Embedded Video Players
While you may want your stream to be available via video players embedded in approved sites, unrestricted use of this feature allows your stream to be embedded anywhere on the internet.
Using a streaming provider that locks your video embed code to specific domains helps you control where your stream can be viewed, while still allowing some freedom to embed the stream within approved sites.
Domain restrictions can be applied on a per-video or per-playlist basis, enabling you to easily separate private streams from content you want to be shared more widely.
Conclusion
No security measure is completely foolproof for enterprise live streaming. This is why businesses need a streaming service with a combination of security tools to make unauthorized access as difficult as possible.
Make sure your live streams and paid content are protected by an enterprise live streaming platform designed for private, large-scale streaming.
References & Further Reading
- Two-Factor Authentication: Who Has It and How to Set It Up
- 6 Tips for Remote Project Managers
- What Is Whitelisting and How Should You Implement It?
- Hacking 2FA: 5 basic attack methods explained
- Enhancing Your Enterprise Security — Do These 5 Things Now

You Can Start Streaming In Less Than 2 Minutes
Try It Free
































![[How To] Set up OBS From A To Z](https://www.streamingvideoprovider.co.uk/assets_dist/svp/img/blog-img/how-to-set-up-use-obs/how-to-set-up-obs-tutorial.png)


DON’T MISS OUT
Get updates on new articles, webinars and other opportunities: